Security is key to AWS outsourcing services
Last updated : September 25, 2019Did you like our article?
Security is key to AWS outsourcing services
IT security, or cybersecurity, is a key element to any company or organization. Data is an asset that demands confidentiality and integrity in outsourcing services, and the availability of data and systems is critical to the operation of business processes.
Processes require ever more that systems allow external or public access over the Internet. At the same time, threats such as unauthorized access, denial-of-service attacks, and ransomware are escalating in the network and multiplying at such a frenetic pace that it is very difficult to keep up with them by permanently implementing new protective measures. An antivirus and firewall are no longer sufficient; the implementation of a comprehensive security framework becomes necessary to protect infrastructure, applications, data at rest and in transit, user access, communications, etc.
Requirements for a secure IT environment
The following elements are key:
- A cybersecurity framework that defines standards, guidelines, and best practices to manage risks associated to cybersecurity. For example, PCI DSS, ISO 27001/27002, CIS Critical Security Controls, or NIST Framework for Improving Critical Infrastructure Security.
- Specified policies, practices, and procedures, in accordance with the adopted framework.
- Proficiency in the implementation of security and its continuous improvement.
- Available technologies to implement security.
How to achieve this
The adoption of a cybersecurity framework, development of policies and procedures, having the necessary skills and technologies, is an effort virtually unattainable for a medium-sized or small company. Fortunately, there are two elements that can save this situation:
- IT services outsourcing, with a provider that contributes, as part of its services, security components such as policies, best practices, procedures, and has the necessary knowledge, experience, and skills.
- A public cloud, such as Amazon Web Services (AWS), that provides infrastructure as a service (IaaS), which is in itself secure (secure datacenter, secure communications, secure physical infrastructure, secure virtualization, etc.), additional secure services (secure databases, secure access control, etc.), as well as the technologies needed to implement cybersecurity at higher levels, where the client is responsible (data, applications, etc.).
Cybersecurity in outsourced services
An outsourced service must consider a shared security responsibility model between the client, the external provider, and the public cloud. For example, AWS is responsible for cloud infrastructure and services security; Novis is responsible for the security of all that is deployed in the cloud (operating systems, applications, networks); and the client is responsible for internal use security policies and standards related to users, roles, and access authorizations to applications and data, and the security of the devices it controls (workstations, mobile devices, communications, etc.).
The cybersecurity framework contemplated in the service must be able to:
- Identify security risks.
- Protect infrastructure, systems, and data from potential security events.
- Detect the effective occurrence of security events.
- Respond to security incidents with planned procedures, communications, mitigation measures, analyses, and improvements.
- Recover normal operations through plans, contingency measures, communications, and improvements.
Cybersecurity tools
AWS provides a wide range of tools and services for security implementation. However, it is necessary to discern which are most adequate and convenient, both technically and economically, and it is also necessary to know how to implement them. AWS’ services are being permanently expanded, so the AWS-based services provider must engage in an ongoing education and training process.
As an example, today AWS provides tools and services for:
- Protection of the datacenter borders from increasingly complex attacks, such as massive denial-of-service attacks (DDoS), or advanced persistent threats (APT) (perimetral security).
- Encryption of data in transit and at rest, throughout the entire lifecycle.
- Events log to monitor and control policies and security incidents in real time and in automated mode (auditability and traceability).
- More than 50 certifications and compliance attestations (see Figure 1).
- Multiple pay-per-use tools, to implement security at different levels (see Figure 2).
Figure 1 and 2:
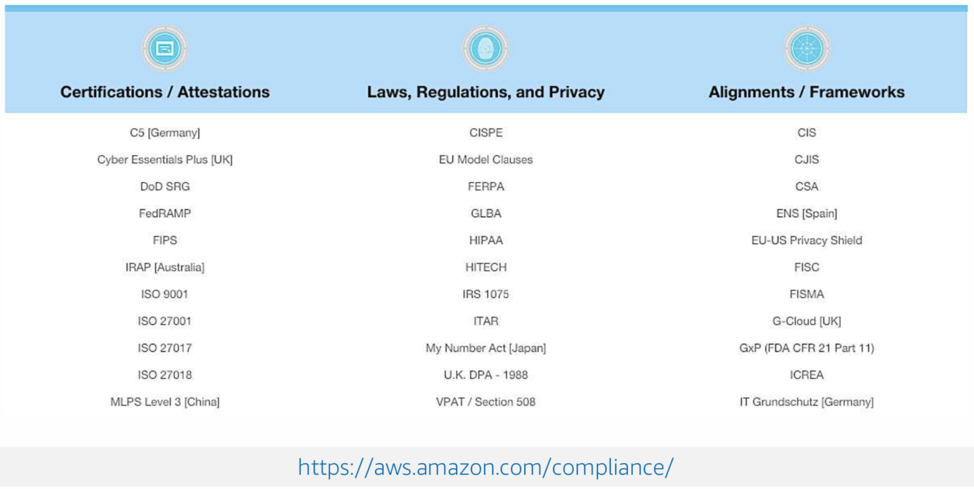
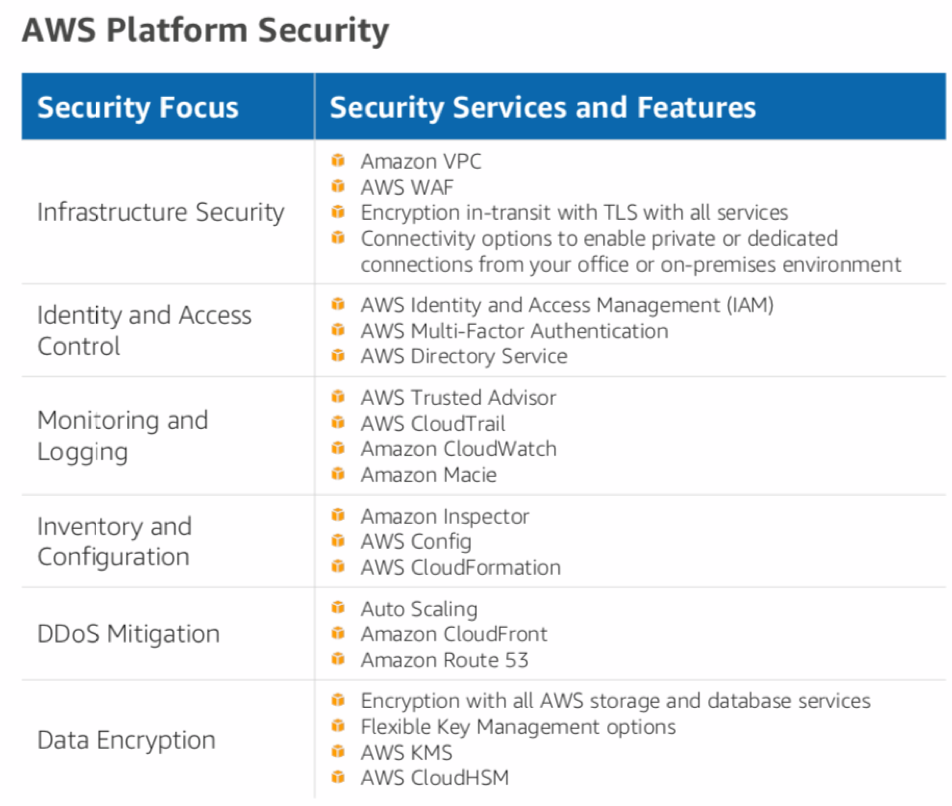
Conclusion
The best solution available today to satisfy the increasing security requirements for existing systems is to outsource with an IT service provider that includes an advanced security model as part of the service.
Services based on AWS’ public cloud offer the best security levels available on the market today, as long as you have a competent provider who has mastered the tools and services, and incorporates best practices in its services.
In this way, the outsourced service not only replaces and existing service, internal or external, but contributes with an enormous value-added component which is a basic need in the current IT environment of all companies and organizations.
If you wish more information about our services, please contact us.
Feedback/discussion with the author, Glen Canessa, Presales Manager at Novis.


