SAP Security Notes – Keeping up to date
Last updated : November 10, 2023Did you like our article?
SAP Security Notes – Keeping up to date
Traditional security measures are not enough to protect SAP systems and their data. One of the flanks to protect is the Security Notes, which SAP releases every month, which we suggest doing through a permanent application to minimize vulnerabilities, as we saw in the article Security in SAP: What are the flanks to protect.
What are SAP Security Notes
Security Notes are small patches that cover, and fix vulnerabilities detected in different components of SAP systems. Vulnerabilities are certain flaws, such as program errors, that could allow a malicious attacker to expose sensitive data, crash the system, or obtain data that can be exploited to initiate another attack. Vulnerabilities are detected by SAP or third parties, and are rated according to their severity in Low, Medium, High and HotNews priorities.
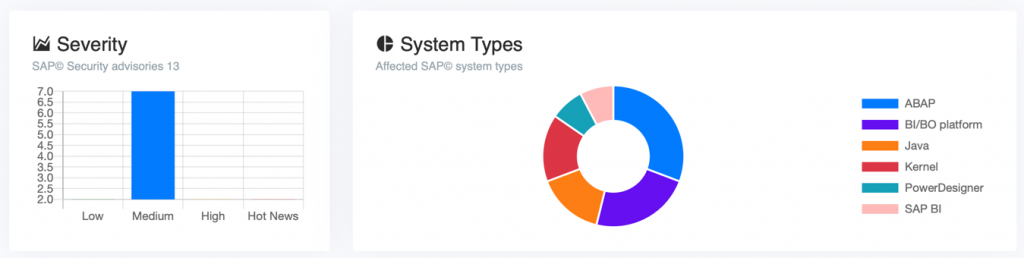
The fixes developed by SAP, or SAP Security Notes, are generally released on the first Tuesday of each month, in its traditional Patch Tuesday. Exceptionally, in the case of a very critical vulnerability, the fix is released immediately, on an individual basis. In addition, all Security Notes are eventually incorporated into the Support Packages Stacks (SPS).
Why we must keep our SAP systems protected
All SAP systems have vulnerabilities in their various components (data engine, Netweaver, Java, ABAP, etc.). The greater the number of vulnerabilities, the greater the attack surface and, therefore, the greater the chances that a malicious attacker will exploit one of these known vulnerabilities to gain access to the system, obtain confidential information, damage, or crash the system, or even hijack an entire database by means of ransomware.
Access to a system for an attack can come from anywhere in the world, in the case of one that is exposed to the Internet; but it can also originate from within a company or institution, or from its suppliers or business partners with enabled access (see for example the case of the hacking of the Chilean Army by a corporal).
So, the attack surface that is exposed in an SAP system increases to the extent that it is not updated, that is, Support Packages or Security Notes released monthly by SAP have not been applied. The direct consequences can be the attacks themselves, in the worst case, but they can also be a poor score in a security audit or a penetration test.
Keeping SAP systems secure
According to SAP Insider’s 2023 Benchmark Report: Cybersecurity Threats to SAP Systems, clients’ top security challenge is keeping systems current with patches and updates.
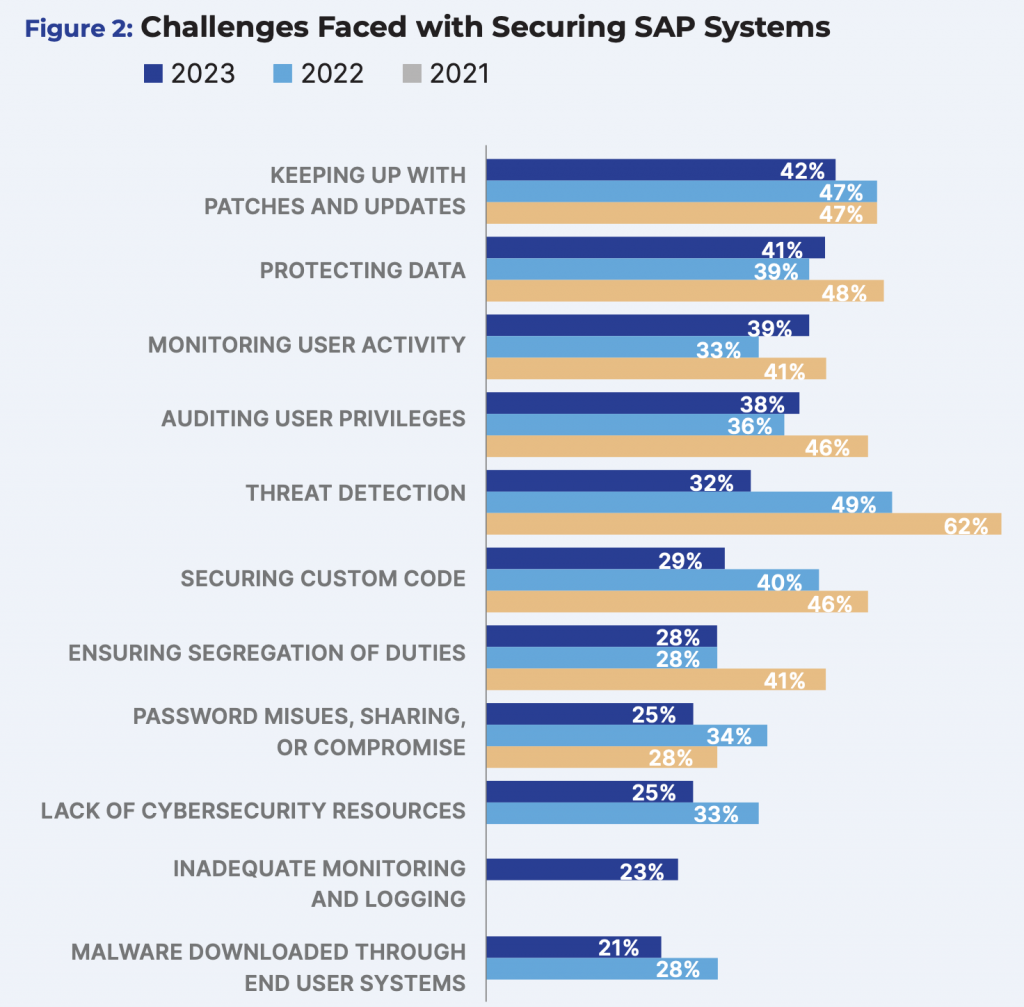
To keep up to date with SAP Security Notes, a constant process is required that includes:
- Ongoing collection of security note information released by SAP.
- Analysis of the notes to determine if they are applicable to the client’s landscape
- Determination and evaluation of the side effects and risks of the implementation of the notes.
- Implementation planning, in coordination with the client.
- Implementation, according to the plan, necessary human resources, and project requirements (e.g., testing).
- Transport to production.
This is a process that is not normally implemented for SAP clients. It is labor-intensive and requires very specific technical and functional skills. Although various tools have appeared to support this process, they do not constitute a solution on their own, as they require technical knowledge of the associated security concepts, in addition to mastery of the tool itself.
For this reason, comprehensive solutions to the different vulnerabilities, in the form of services delivered by a specialized provider, are more effective.
Novis offers a standardized service for the permanent application of SAP Security Notes, structured according to SAP best practices, and based on recognized SAP Vulnerability Management tools. This service can be delivered to any SAP systems client, regardless of whether their systems are In House, in Private Hosting, in Public Cloud, in SAP HEC, in RISE, etc.
For more information on this and other of our security services we invite you to contact us.
Author: Glen Canessa.
Related notes


